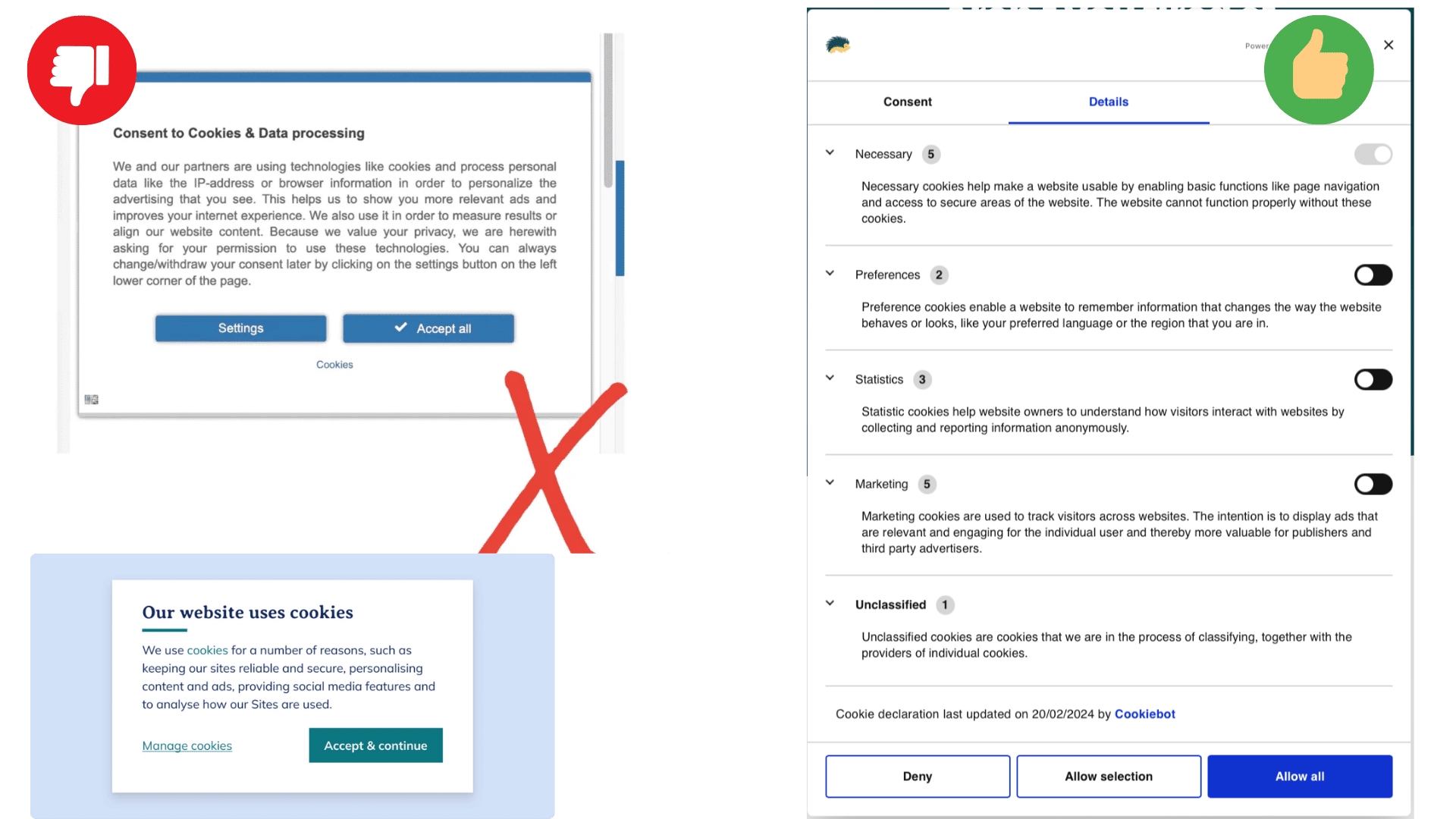
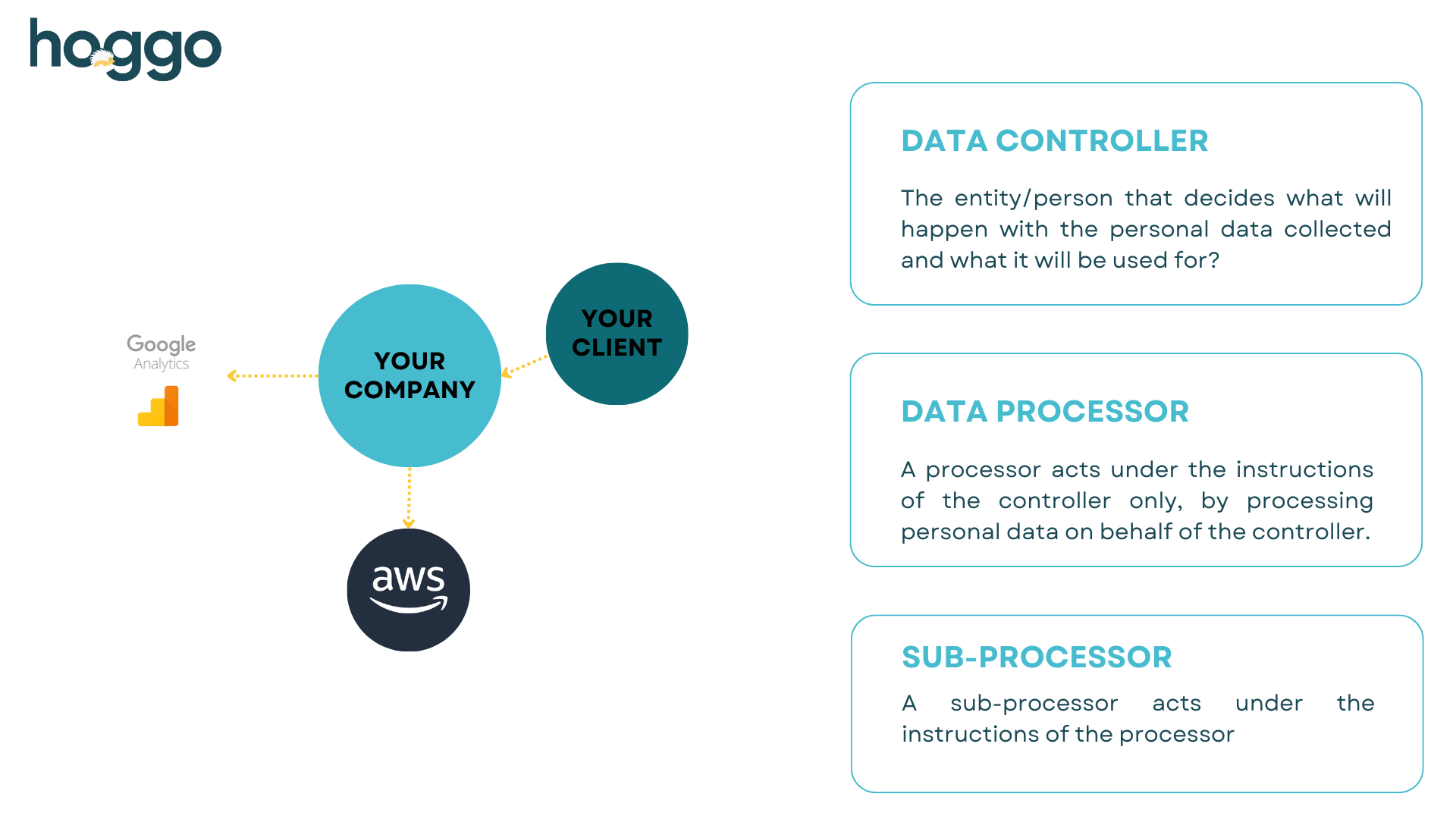
How to create a compliant RoPA?
Article 30 lays out the form of a RoPA. It should be in writing and in an electronic form, so it is amenable to changes and edits as may be necessary from time to time.
As such, Microsoft Excel Sheets and Google Spreadsheets are usually the first port of call for most privacy teams/DPOs.
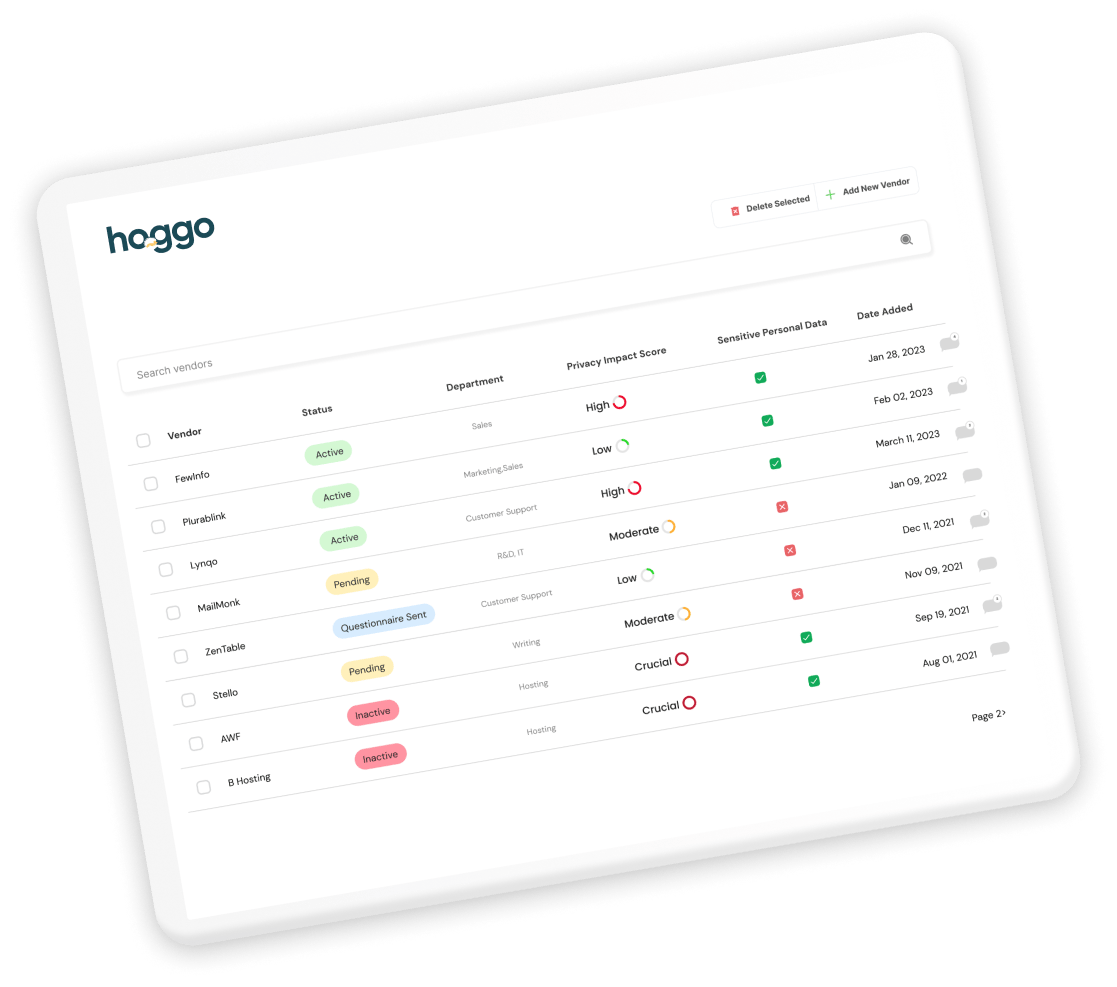
However, they are usually long, hectic, and hard to navigate. Luckily, you can use hoggo’s My Vendors and export a dedicated vendor RoPA which maps your data flows with and to your vendors.
Whichever solution you go with, here’re a break down of the steps involved in creating a compliant RoPA:
Preliminary step: Data Mapping
A comprehensive data audit or data mapping exercise helps you uncover what data your organization holds and where. In other words, it helps you map personal data flow and processing activities at all levels.
Very often, companies would engage external consultants for the initial mapping of RoPA and deploy DPO-as-a-Service solutions for ongoing DPO duties.
Data Mapping is within the job description of your Data Protection Officer (DPO). But in the absence of a DPO, any employee with the necessary qualifications can perform this task.
The mapping process involves identifying information systems and personal data to understand the data held and its locations within the organization; Involve key internal stakeholders across departments to ensure a wide coverage and to avoid information gaps in your findings.
Compile a survey/questionnaire
Launch an inquiry into departments in your company that handle personal data. Keep things simple with your questioning. You could ask questions like:
- How do we use personal data?
- Who do we collect personal data from?
- What personal details do we have about them?
- Who do we share this information with?
- How long do we keep this data before deletion?
- How do we protect personal information?
Interview Key Stakeholders
Secure the buy-in of your higher-ups and other key stakeholders within the organization. Doing this achieves two things:
- They understand the import of your data mapping exercise; and
- They share more insight into how data is being processed by certain parts of your organization.
For instance, IT staff could answer on technical security measures, and Information governance staff can reveal more about retention periods. Equally, legal & compliance staff can lay out the full repertoire of data-sharing arrangements struck with other third parties.
Review policies, procedures, and agreements
Besides the legal due diligence you will be carrying out, you can benchmark your actual processing practices against industry best practices. A few of the documents you should be looking at here are:
- Data protection policies
- Data retention policies
- Privacy policies
- System use policies
- Data processor contracts
- Data sharing agreements
- Data security policies
Document your findings
At risk of sounding like a broken record, your documentation must be in writing, which may come in electronic or paper form.
One rewarding perk of the electronic form is the ability to add, subtract, and edit your documents as necessary, which makes it the natural fit for companies with very frequent processing activity.
In any case, you want a granular inventory of all your processing activities based on a data mapping exercise that is reviewed regularly.
The test for granularity here is sufficient context. Delineate personal data into separate categories, stating their respective purposes and attributes.
For example, data retention periods might differ across a vast range of categories of data. Reflecting this in your documentation will give the viewer as much structural and contextual meaning as possible.
To achieve full compliance, steer clear from generic descriptions with no meaningful context to meet compliance requirements. For your continuous documentation needs, you can ditch the traditional survey and spreadsheets for a dedicated data mapping automation (SaaS) solution with these functionalities:
- Central management of data from one secure dashboard;
- Integrates seamlessly with other systems;
- Automated Data removal;
- Seamless collaboration throughout all department;
- DPO control panel + segregation of ownership of activities; and
- Tracking changes in data.